6. Challenges
Use the form in item 4 above to inject usernames that do the things below.
For hints, see the "Sources" at the bottom of the page.
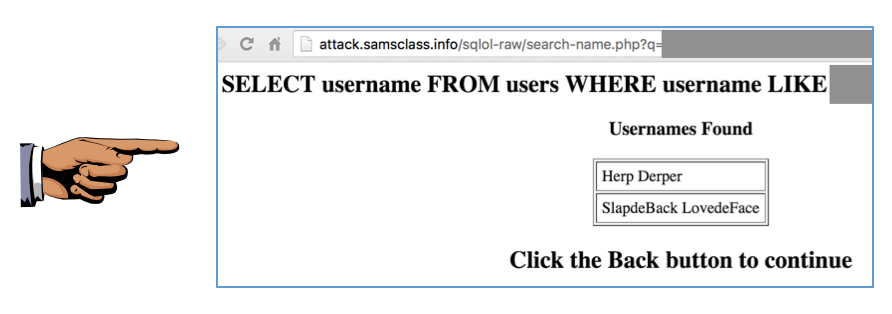
Challenge 1: Display names for administrators only,
as shown below:
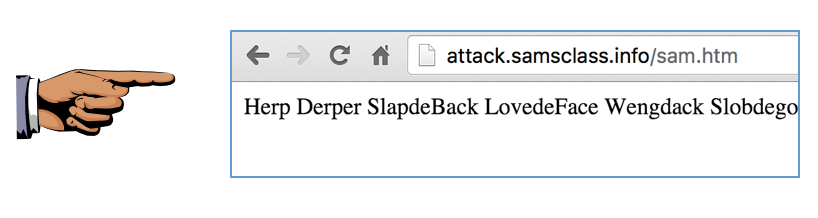
Challenge 2: Create a file on my server with your name as a filename,
as shown below.
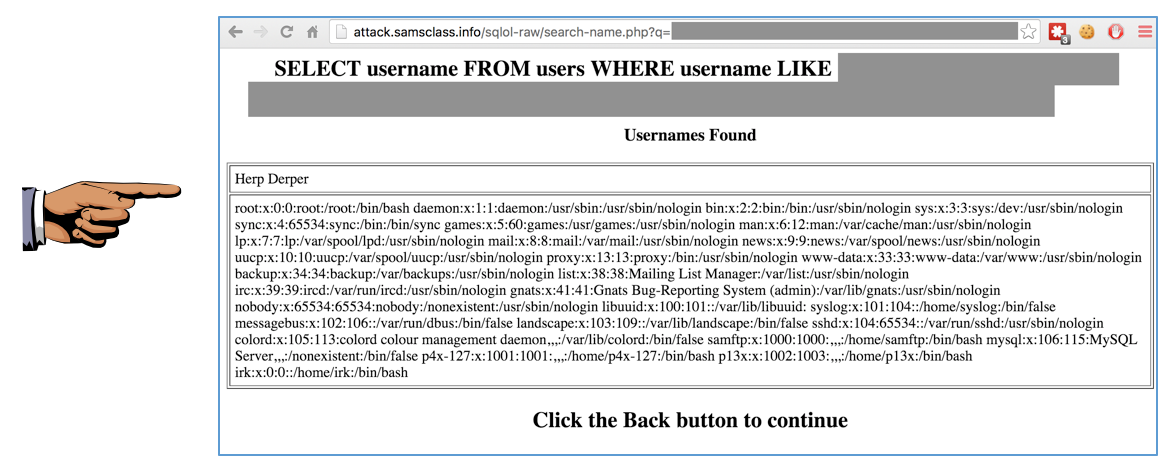
Challenge 3: Display the /etc/passwd file in a browser,
as shown below:
Challenge 4: Put your name into these two files:
/var/www/html/SQLchal/winners
/var/www/html/SQLchal/updatenow
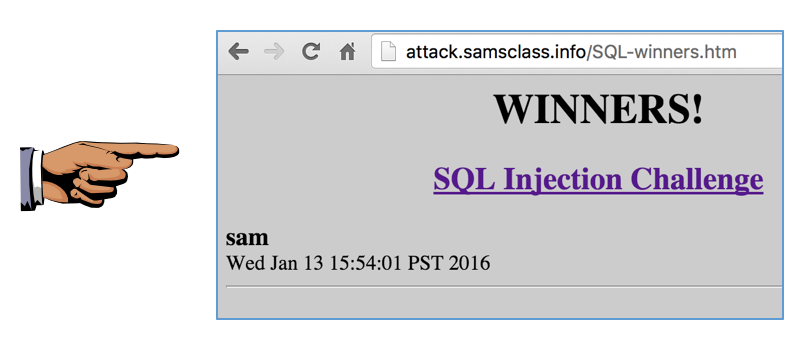
Within a minute, your name will appear on
the
Winners page
as shown below:
Challenge 5: Use a different server, without the
option to use raw SELECT queries.
Before starting, click the button below
to reset the database:
Now use this name search form:
Put your name into these two files on that server:
/tmp/SQLchal/winners
/tmp/SQLchal/updatenow
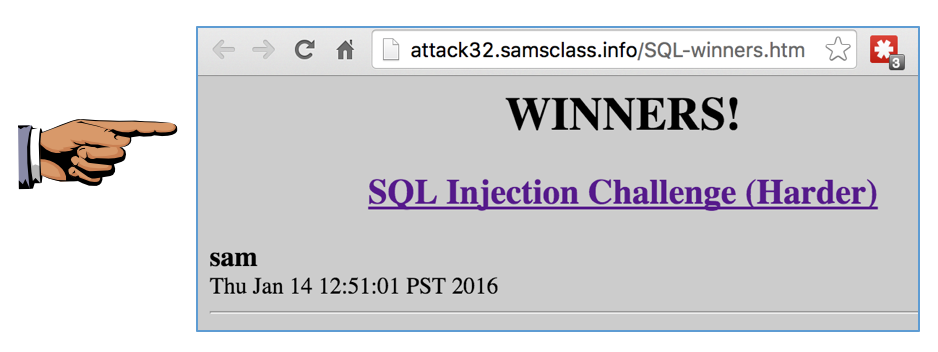
Within a minute, your name will appear on
the
Winners page
as shown below:
|